
If you’re here reading this you’ve probably already heard about the log4j vulnerability and you’re wanting to eliminate it in your environment.
This article just focuses on Windows server. The first thing you should do is to update any applications using old versions of log4j-core-2.x.x.jar to the latest versions. log4j-core-2.16 at this time. Speak to your software vendors about this.
If an update is not possible or requires more time you can mitigate the vulnerability by removing the java class that is used in the exploit. Use the following instructions.
Manual Steps:
1. Search your server for any files with the name log4j-core-2*.jar. In this example I will use a file from the application Tableau.
Directory: C:\Program Files\Tableau\Tableau Server\packages\lib.XXXXXXX\log4j-core-2.1.jar
2. Using file explore navigate to the directory with the outdated log4j-core-2x file and rename the extension from .jar to .zip
Note: I recommend taking a copy and renaming it as .backup in case you need to restore it.
3. Open it up with file explorer and click down to the following path. “org\apache\logging\log4j\core\lookup\”
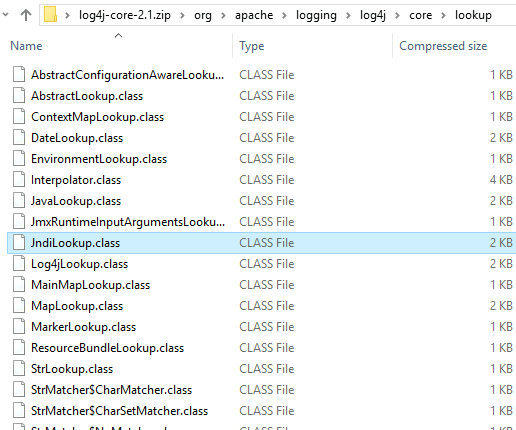
4. Right click and delete the file “JndiLookup.class”
5. Now rename the zip file back to .jar
6. Restart your application or server for this change to take effect. Once back online the exploit should not be able to be executed against this server, effectively mitigating the risk of a hacker / bad actor using this exploit. It is highly recommended to update to the 2.16 version or higher as soon as possible.
Automated with Powershell:
It is also possible to mitigate this using Powershell and build a script to apply it over a large environment once you have a list of the servers and directories with out of date log4j-core files. The basic commands to do this are the following.
<#
.SYNOPSIS
Removing the JndiLookup.class from old log4j-core file using powershell
.DESCRIPTION
A very basic script to remove JndiLookup.class from old log4j-core files to mitigate the log4j hack
.NOTES
Author: Phillip Puggioni
Website: https://philpug.com
License: GNU GPL v3 https://opensource.org/licenses/GPL-3.0
#>
# Variables
# Replace with the correct path for your application
$Path = "C:\temp\log4j-core-2.1.jar"
$split_path= $Path.Split('\')
$filename = $split_path[$split_path.Count-1]
$JndiLookup_class = "org\apache\logging\log4j\core\lookup\JndiLookup.class"
$destination_folder = $path.Replace("\"+$filename,'')
$Export = $destination_folder + "\" + $filename.Replace('jar','export')
<#
The section will take a backup of the file, rename it to a zip file, expand the zip, remove the class and repackage it back to a jar file.
#>
try{
Copy-Item -Path $Path -Destination ($destination_folder + "\" + "log4j-core-2X-Backup") -Force
Rename-Item -path $Path -newname $filename.Replace('jar','zip') -Force
New-Item -Path $destination_folder -Name $filename.Replace('jar','export') -ItemType Directory -Force
expand-archive -Path $Path.Replace('jar','zip') -DestinationPath $Export -Force
Remove-Item -Path ($Export + "\" + $JndiLookup_class) -Force
Compress-Archive -Path ($Export + "\*") -CompressionLevel Fastest -DestinationPath ($destination_folder + "\" + $filename.Replace('jar','zip')) -Force
Rename-Item -path $Path.Replace('jar','zip') -newname $filename.Replace('zip','jar') -Force
Remove-Item -Path $Export -Recurse -Force
}
catch {
$Error[0] | Out-File c:\temp\errors.txt -Append
}
https://github.com/philpug/Powershell_scripts/blob/master/vulnerability_mitigation/log4j_Class_Removal.ps1
Note: This is a very basic script. I recommend reviewing and rewriting it to meet your environment’s needs.

Nice one, Phil. Clear, concise, and to the point. I’ve used this process on a couple of legacy VM’s I’ve pulled off ice from BEFORE this exploit was known … very appreciative, thanks!
Many thanks for the kind words, glad to hear it helped you.