Goal:
Limit the permissions on an OU or sub OU to so that the Account Operators group does not have access to make any changes to the users in the OU
Problem:
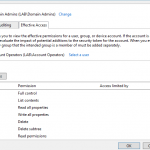
Even with the Account Operators removed from the OU or set to Read Only Permissions they still have full access to make changes to new and existing user accounts in the restricted OU.
Environment:
Windows Server 2012 R2 STD Active Directory
Cause:
The Account Operators is a privileged group whose permissions are controlled by the AdminSDHolder object. All members of the group are protected by default. A process called SDProp runs once per hour on the DC with the PDC Emulator FSMO role to make sure permissions match those assigned to the AdminSDHolder object. One of the things this protection does is to disable inheritance, so the protected members do not get the permissions assigned to any parent OU’s.
Work Around:
The protection can be removed from Account Operators by modifying the dSHeuristic attribute of the cn=Directory Service object in the cn=Windows NT,cn=Services container in the Configuration partition of the forest
This Wiki article explains:
https://social.technet.microsoft.com/wiki/contents/articles/33307.active-directory-find-orphaned-objects.aspx
Critical note:
Microsoft recommends the following for the Account Operators built-in group
“As a best practice, do not add members to this group, and do not use it for any delegated administration.”
Source: (https://msdn.microsoft.com/en-us/library/cc875827.aspx#XSLTsection124121120120)
Solution:
To maintain best practices in the environment, a new security group should be created and all the users previously in the Account Operators group moved to the new security group. The new group needs to have the correct permissions to manage the other OUs delegated to it.