This post will not answer the question of if you need to use https for WinRM in your environment. For the answer to that question you can find the a detailed breakdown in this blog post – Link by foxdeploy.
In short it’s mostly only important in environments were the remote server or workstation is not running on the domain. For example in DMZs.
For these instructions it’s assumed that you have a Windows Certification Authority running in your environment and the root certificate has already been deployed to the Trusted Root Certification Authorities location on both machines.
Lets get started
Connect to the server on which you want to enable WinRM over HTTPS. The first step is to create a certificate for the server from your internal certification authority. Depending on how the server is setup to communicate with the domain there are a number of different ways to do this. If domain connected to can make the request through the certlm.msc, certificate request site or commend prompt.
I will note correct this step in detail but it’s important that the certificate’s subject name is the same as the computer netbios name(workgroup) or FQDN(domain joined).
You can use the Web Server Template in your certificate templates store, or ideally duplicate your web server template and configure it as its private key exportable.
If you had to manually request the certificate from another device and move it to the server because it’s in an isolated network, then install the certificate in local computer > Personal > Certificates
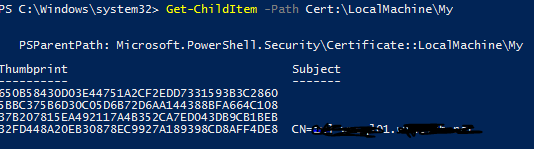
Open up a Powershell terminal as a local administrator and run the following:
Get-ChildItem -Path Cert:\LocalMachine\My
The new certificate and computer name should be displayed
At this point you’re ready to setup WinRM over HTTPS with one command
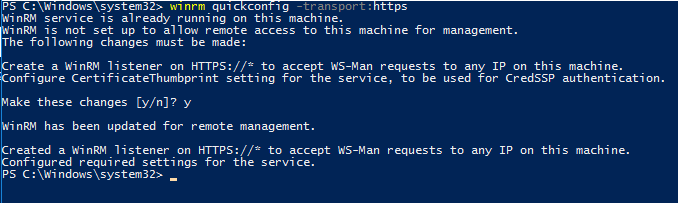
If it has never need configured before you’ll have to enable it. The simplest way to do this is with the WinRM quickconfig
winrm quickconfig -transport:https
The result should look something like this
If you have previously setup winrm on the machine before you’ll most likely have a http listen. To be truly restricted to https only you should remove the http listener. Can check what listeners exist and remove the http listener with the follow command.
#View winrm listeners
Winrm enumerate winrm/config/listener
#Remove the http listener
winrm delete winrm/config/Listener?Address=*+Transport=HTTP
#Options for more info about the config
Winrm get http://schemas.microsoft.com/wbem/wsman/1/config
Note: the last command will also show if the listener is for some reason configured to allow unencrypted traffic.
Now it’s configured you can safely connect to the server over a connection that is protected by both https and kerberos encryption.
It’s important to note that when you now connect to the server running WinRM over HTTPS via PSSession or invoke-command you need to always use the -UseSSL flag
#Example 1
Enter-PSSession -ComputerName MYSERVER -Authentication Default -UseSSL
#Example 2 with port flag
Enter-PSSession -ComputerName MYSERVER -Authentication Default -UseSSL -Port 5986
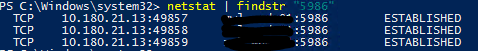
Finally, once you connect to test it from another server via Enter-PSSession you should be able to prove that it’s using the https port for WinRM. This can be done with the following command.
netstat | findstr "5986"
The results should look like this if successful.